new cyber threats for hyper-connected ships
The rapid introduction of hyper-connectivity through Starlink, OneWeb, and other LEO services presents a pressing challenge for shipping companies, necessitating significant enhancement of their cybersecurity measures to effectively mitigate the evolving threat landscape.
Maritime Hyper-Connectivity Framework

The Maritime Cyber Connectivity Framework is a vital tool for understanding risks and vulnerabilities while enhancing cybersecurity readiness in the age of heightened connectivity at sea.
The Five Cyber Attack Vectors You Need to Consider
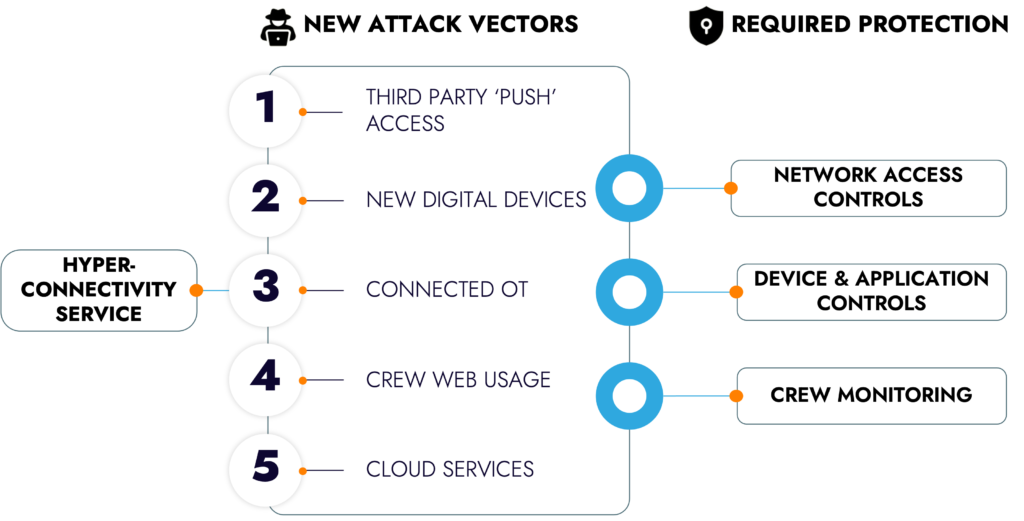
01
Third Party ‘Push’ Access
Updating devices, once a slow but secure manual process, has been revolutionized by maritime hyper-connectivity. With speed and ease, however, come new cyber vulnerabilities for malicious updates to be automatically pushed through unnoticed.
02
New Digital Devices
While more technology can greatly improve the safety, efficiency, and sustainability of a vessel, it creates previously unconsidered cyber vulnerabilities that demand overhauled safeguards for devices and networks.
03
Connected OT
As maritime OT devices progress into the realm of connected technology, new protocols and access methods open doors to system vulnerabilities. With increased connectivity comes an urgent need to rethink system protection.
04
Crew Web Usage
As the vast majority of shipping companies provide onboard crew internet connectivity through satellite networks, new attack vectors like phishing and malware from compromised apps and websites arise. This requires new defenses, like crew network isolation and constant network security monitoring to ensure the protection of a vessel’s essential systems.
05
Cloud Services
Benefactors of maritime hyperconnectivity have jumped on the opportunity of cloud service implementation. This enhanced convenience, however, destroys the ‘internal-external’ perimeter of the past with vulnerable cloud technologies that demand overhauled cybersecurity measures for proficient protection.
The Three Layers of Cyber Protection You Need to Adopt
01
Network Access Controls
To address the growing diversity of devices and users, we implement enhanced network segregations, access controls, and comprehensive monitoring of an expanded range of network protocols, mainly focusing on Operational Technology (OT). This is also mandated by new maritime cybersecurity regulations.
02
Device and Application Controls
New attack surfaces introduced with hyper-connectivity and the service it enables cannot be solved by network monitoring only. Devices must be scanned for vulnerabilities, and their usage must be monitored, as compromised devices can produce seemingly legitimate traffic with abnormal patterns.
03
Crew Monitoring
With limited connectivity, segregating the crew network was usually sufficient as there was little activity from crew devices. However, hyper-connectivity opens the door for new risks. We recommend paying specific attention to crew usage because social engineering methods are so commonly used for exploitation.
Cyber Protection Infrastructure
- Implement threat detection and unauthorized access monitoring, covering internal and external traffic, encompassing all user types and assets.
- Segregate networks and constantly monitor the integrity of network segregations, in real-time.
- Create a comprehensive map, monitor, and conduct vulnerability checks for all maritime assets, including Information Technology (IT) and OT assets.
- Implement real-time anomaly detection at an individual asset level.
- Conduct training and awareness programs for the crew to enhance their cybersecurity knowledge.
- Implement real-time usage monitoring to identify and mitigate potential threats.
The Importance of Assessing Cybersecurity Risks Before Enhancing Connectivity
Higher bandwidth offers improved speed and capabilities in the dynamic realm of digital connectivity. Yet, it underscores the critical importance of heightened cybersecurity. This scenario mirrors past technological transitions, like the shift from dial-up to broadband and later from broadband to high-speed fiber connectivity. Each leap in connectivity demands a reassessment and reinforcement of cybersecurity measures to counter emerging threats effectively.
